Cyber Security
Wherever your business goes, whoever it works with, you need cybersecurity that covers it all.
To contend with hackers, you have to become one.
We work with you to assemble custom red teams comprised of creative thinkers and top information specialists. Their job is to test your defenses through real-world attack simulations, helping you understand and imagine how information can be uniquely externalized and exploited by adversarial forces.
Watch us get behind the keyboard and inside the minds of cyber attackers to help corporations stay ahead of every move.
Combining managed security services, market-leading advanced analytics and intelligent automation, our cyber defense incubation centers help organizations out-innovate attackers every single day.
Our security program solutions are designed for short-term and long-term services. Whether it is an annual penetration test or an ongoing virtual CISO engagement, our team of cyber security consultants are here to assist.
Our Business Goal
To be the trusted partner for organizations seeking excellence in leadership, operational efficiency, and transformative growth.
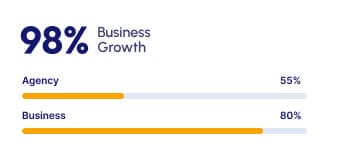
Why choose our Cyber Security Service
Your customers trust you with their security. Who do you trust? The threats of cyber attacks are a fact of life and a fact of business - and your customers know it. ARKIN TECHNO Cybersecurity and Risk Service can help you stay ahead of the threats and put your customers minds at ease. We take an integrated approach to protection that prioritizes not only prevention, but also minimizing risk and controlling loss. Our portfolio of Cyber Defense Platforms is designed to deploy the right solutions to keep your company protected, and resilient, whatever the circumstances.
Key Trends in Cyber Security
AI and Machine Learning for Threat Detection : AI helps identify anomalies, analyze patterns, and detect emerging threats faster and with higher accuracy.
Zero Trust Architecture : Never trust, always verify approach to security, treating all users and devices as potential threats until verified.
IoT Security : As IoT devices proliferate, securing them becomes crucial due to their vulnerability and potential entry points for attacks.
Cloud Security Advancements : With more organizations adopting cloud computing, security strategies that protect data across hybrid and multi-cloud environments are essential.
Threat Intelligence Sharing : Organizations are increasingly sharing threat intelligence to better understand emerging threats and improve defenses collectively.
Automated Security : Automating routine security tasks, like patching, monitoring, and incident response, improves response times and reduces the workload on cybersecurity teams.